LeaksID
5/5 (out of 6 reviews ) | ???? 1882 installs | ???? N/A
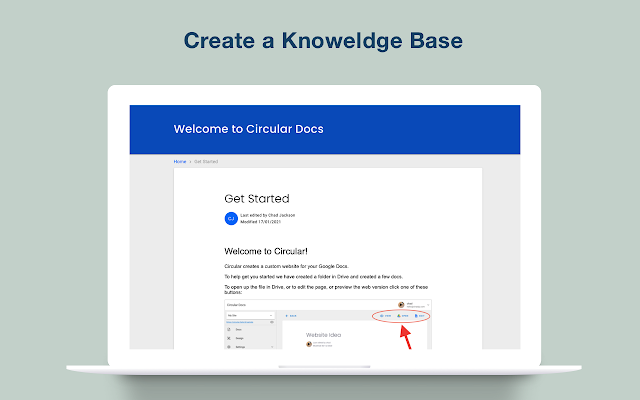
LeaksID is a cloud-based solution that deters malicious users from leaking valuable data. You can now share documents securely and identify the person responsible in case of a leak.
Frequently Asked Questions
1. What is the rating of the LeaksID?
The LeaksID has a rating of 5 out of 5 based on 6 reviews.
2. How many active users does the LeaksID have?
The LeaksID has a user base of 1882 active users.
3. What is the cost of the LeaksID?
The cost of the LeaksID is N/A.
4. How to download the LeaksID?
To install LeaksID follow the below step:
- Visit the following link: LeaksID
- Click on the “Install” button located on the right side of the page.
- A prompt will appear requesting access permissions for the addon. Review the permissions requested
and click on the “Continue” button. - If prompted, choose the Google account associated with your Google Workspace or Gmail account that
you want to use with the addon. - Review the permissions again and click on the “Allow” button to grant the necessary permissions.
- The installation process will begin, and you’ll see a progress indicator.
- Once the installation is complete, you’ll see a confirmation message indicating that the LeaksID
addon has been successfully installed to your account. - You can now access the addon. The specific steps to use the addon will depend on its functionality.
Refer to the addon’s documentation or instructions provided by the developer for guidance on how to
use it effectively.
Top Keywords that are used in the LeaksID addon’s description :
| Keyword | Count |
|---|---|
| document | 8 |
| leaksid | 5 |
| leak | 4 |
| documents | 4 |
| share | 4 |
| data | 3 |
| works | 3 |
| identify | 3 |
| work | 3 |
| proprietary | 2 |
| technology | 2 |
| core | 2 |
| via | 2 |
| cloud-based | 2 |
| files | 2 |
| Keyword | Count |
|---|---|
| proprietary technology | 2 |
| technology core | 2 |
| leaksid cloud-based | 2 |
| invisible marks | 2 |
| marks document | 2 |
| data leaks | 2 |
| online data | 1 |
| data leak | 1 |
| leak deterrence | 1 |
| deterrence system | 1 |
| system proprietary | 1 |
| core deters | 1 |
| deters malicious | 1 |
| malicious users | 1 |
| users leaking | 1 |
| Keyword | Count |
|---|---|
| proprietary technology core | 2 |
| invisible marks document | 2 |
| online data leak | 1 |
| data leak deterrence | 1 |
| leak deterrence system | 1 |
| deterrence system proprietary | 1 |
| system proprietary technology | 1 |
| technology core deters | 1 |
| core deters malicious | 1 |
| deters malicious users | 1 |
| malicious users leaking | 1 |
| users leaking sensitive | 1 |
| leaking sensitive documents | 1 |
| sensitive documents screenshots | 1 |
| documents screenshots photos | 1 |